
AMD is investigating a report published today by an Israeli security firm disclosing the presence of 13 security flaws affecting AMD Ryzen and EPYC processors.
The 13 vulnerabilities are organized across four vulnerability classes named RyzenFall, MasterKey, Fallout, and Chimera.
CTS Labs, the security firm who discovered these flaws, claims they can provide attackers with full control over a system, but also allow attackers to extract data from secure areas of AMD CPUs, similar to the now-infamous Meltdown and Spectre flaws.
Security firm notified AMD only yesterday
Patches are not available, as AMD is still investigating the report. According to reports, CTS Labs allegedly notified AMD of the flaws only yesterday, and AMD hasn't even confirmed that the report contains valid findings.
CTS Labs claims to have discovered the flaws when it analyzed a modern AMD CPU and spotted what appeared to be the backdoor code it previously discovered in old ASMedia firmware. This sparked a more in-depth investigation that later unearthed 13 security bugs.
These flaws and the processors they affect are detailed in the image below. CTS Labs says some flaws could affect more AMD processor series, as they have not attempted to create proof-of-concept exploit code for all CPU series.
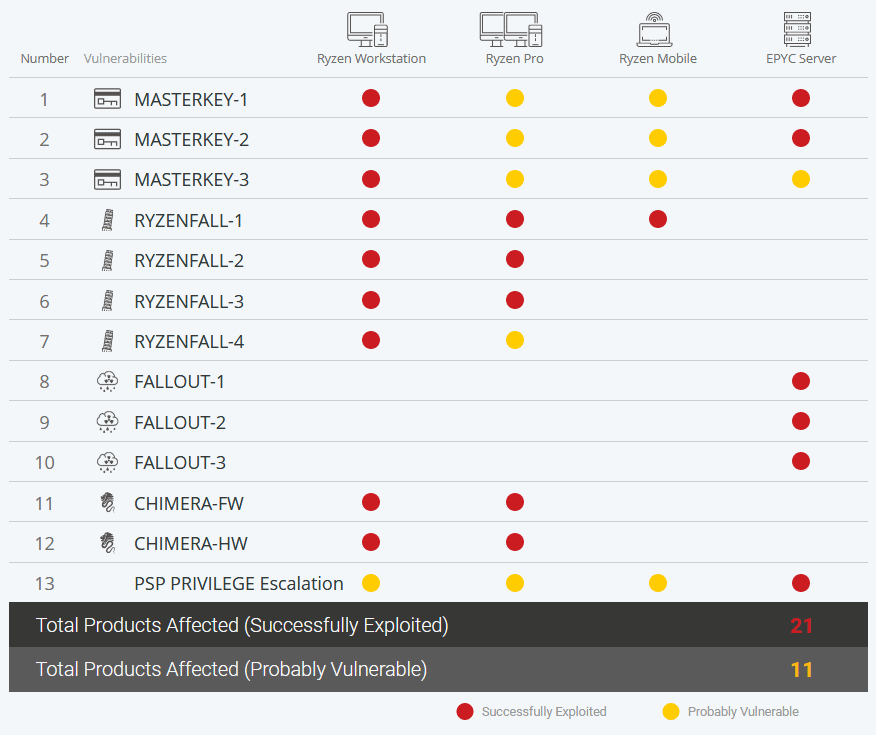
The affected AMD CPUs are deployed in desktops, notebooks, smartphones, and servers alike. CTS Labs claims to have notified AMD, Microsoft, and a small number of OEMs, so they could get started on creating patches.
What are these vulnerabilities?
Below is a description of what CTS Labs researchers claim the vulnerabilities allow an attacker to perform. Just bear in mind, AMD has not confirmed any of these just yet.
MasterKey 1, 2, 3
⏺ Bypass firmware-based security features such as Secure Encrypted Virtualization (SEV) and Firmware Trusted Platform Module (fTPM)
⏺ Network credential theft. Bypass Microsoft Virtualization-based Security (VBS), including Windows Credential Guard
⏺ Physical damage to hardware (SPI flash wear-out, etc.)
⏺ Affects: EPYC, Ryzen, Ryzen Pro, Ryzen Mobile. Successfully exploited on EPYC and Ryzen.
RyzenFall 1 and Fallout 1
⏺ Network credential theft. Bypass Microsoft Virtualization-based Security (VBS) including Windows Credential Guard
⏺ Enables memory-resident VTL1 malware that is resilient against most endpoint security solutions
⏺ Affects: EPYC, Ryzen, Ryzen Pro, Ryzen Mobile. Successfully exploited on EPYC, Ryzen, Ryzen Pro and Ryzen Mobile.
RyzenFall 2 and Fallout 2
⏺ Enables memory-resident SMM malware, resilient against most endpoint security solutions
⏺ Affects: EPYC, Ryzen, Ryzen Pro. Successfully exploited on EPYC, Ryzen, Ryzen Pro. Ryzen Mobile is not affected.
RyzenFall 3 and Fallout 3
⏺ Network credential theft. Bypass Windows Credential Guard by reading secrets from VTL1 memory
⏺ Affects: EPYC, Ryzen, Ryzen Pro. Successfully exploited on EPYC, Ryzen, Ryzen Pro. Ryzen Mobile is not affected.
RyzenFall 4
⏺ Bypass firmware-based security features such as Firmware Trusted Platform Module (fTPM)
⏺ Network credential theft. Bypass Microsoft Virtualization-based Security (VBS), including Windows Credential Guard
⏺ Physical damage to hardware (SPI flash wear-out, etc.)
⏺ Affects: Ryzen, Ryzen Pro. Successfully exploited on Ryzen, Ryzen Pro.
Chimera (Firmware, Hardware versions)
⏺ Allows malware to inject itself into the chipset’s internal 8051 architecture processor
⏺ The chipset links the CPU to USB, SATA, and PCI-E devices. Network, WiFi and Bluetooth traffic often flows through the chipset as well
⏺ Malware running inside the chipset could take advantage of the chipset’s unique position as a middleman for hardware peripherals
⏺ Affects: Ryzen, Ryzen Pro. Successfully exploited on Ryzen and Ryzen Pro.
CTS Labs facing criticism
The CTS Labs team has put considerable efforts into marketing these security flaws, with the creation of a dedicated website and the release of professionally-shot YouTube videos.
The infosec community is more than displeased with the company's decision to give AMD only one day to address these flaws and with the fact they did not share any technical write-up to prove their research's validity. Furthermore, some experts also pointed out that the company is overhyping the vulnerabilities, all of which require admin-level access for successful exploitation.
First read of the AMDFLAWS whitepaper (no real technical details given) is: “over-hyped beyond belief”.
— Arrigo Triulzi (@cynicalsecurity) March 13, 2018
This is a whitepaper worthy of an ICO.
And yes, that is meant to be an insult.
"Exploiting MASTERKEY requires an attacker to be able to re-flash the BIOS with a specially crafted BIOS update." lol yes well
— Jeff Kampman (@jkampman_tr) March 13, 2018
Some security researchers also pointed to a particular section of the CTS Labs website's legal disclaimer, shortly after it became evident that AMD stock took a 2% price tumble.
CTS Labs states that it did not put users at risk by disclosing these flaws without giving AMD a chance to confirm and issue patches. The company claims that only it and AMD have the technical details needed to exploit these vulnerabilities and that users are still secure.
UPDATE [March 13, 17:00 ET]: AMD has issued an official statement on CST's findings, revealing it is still investigating the incident. In addition, a CTS Labs spokesperson confirmed to Bleeping Computer that Trail of Bits CEO Dan Guido had reviewed their findings for accuracy. Guido confirmed today that the security flaws are real, albeit not as severe as they might sound, as they do require admin-level access to exploit.



Comments
pccobbler - 6 years ago
This story smells of hedge fund parasites. As The Register reported: "John Fraser Perring, founder of Viceroy Research, which describes itself as 'a group of individuals that see the world differently,' confirmed to The Register that his firm has a short position in AMD stock and that he intends to increase that position in light of support for CTS-Labs' findings."
the_moss_666 - 6 years ago
Viceroy Research is well known di*khead. Stock price manipulation is what they do for a living. Look at https://www.businesslive.co.za/bd/companies/2018-01-12-the-phantom-faces-behind-the-viceroy-research-reports-remain-hidden/ .
Quote: "Stocks including Africa’s largest generics drugmaker and biggest real-estate investment trusts were sent reeling this week on speculation that they were in Viceroy’s sights. More than $3bn was wiped off the value of property stocks alone in just four days..."
It's the same scheme with AMD, but now they are using another company to leave their dirty name out of the report.
_LC_ - 6 years ago
Yes, I wish it wouldn't be this easy. Why is this crap being propagated everywhere? :-P
the_moss_666 - 6 years ago
Brief summary:
- Masterkey
Ability to change BIOS is already game over condition, despite CPU architecture. There is room from improvement, but it's not AMD fault (or AMD architecture flaw)
- RYZENFALL and FALLOUT
Signed drivers has priviledge access to CPU and can be misused to do bad things. So what's new and why is this AMD specific flaw?
- CHIMERA
Some third party components may be vulnerable and can contain backdoor. Why is this a flaw of AMD architecture? Also, CTS never said there is any known vulnerability or backdoor. They said there could be backdoor, which is true for every manufacturer using any third party component.
Plus there is a disclaimer, saying that nothing in the report is a statement of fact, so thechnically, these flaws dosen't actually exist. Report just says it might be possible to modify computer to use its computing powers for Evil.